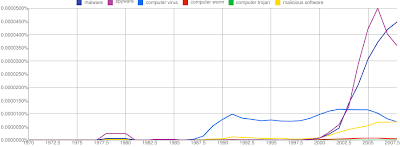
Yesterday, Google released a rather addictive tool on GLabs that graphs the rate of occurrence of particular phrases in around 10% all books ever published in the a number of languages.
It is interesting to see how some security topics/keywords have entered the mainstream (of written publications) or perhaps are leaving it.
Information Security vs Cyber Security vs Data Security vs etc...
Malware vs Virus vs Trojan vs etc...
Identity Theft Advent.
Just For Fun...